Virtual Circuits
Virtual circuits are created within circuits in the policy tree and are used to logically divide or partition the circuit. The virtual circuit defines what traffic will be processed in this partition and how much bandwidth it is allowed. The virtual circuit can enforce fair sharing amongst the network hosts. Traffic is evaluated against the definition of the virtual circuit. Traffic that does not fall within the virtual circuit is evaluated by the next virtual circuit and so on. Each virtual circuit will have it's own set of policy rules.
The following are common use cases for virtual circuits.
- Virtual circuits are configured to allocate bandwidth or specify policy rules for each branch office or service provider's customer.
- Separate virtual circuits are configured for WAN data and for Internet data.
- Separate virtual circuits are configured for inbound traffic and for outbound traffic.Virtual circuits cannot be asymmetric, so this technique will accommodate the need for asymmetric partitioning of the circuit.
- Separate virtual circuits are configured for different aspects of your network for monitoring purposes. For instance, one virtual circuit could be configured to control and monitor your wifi network, and another to control and monitor your servers, and another to control and monitor your back-office computers.
- A virtual circuit can enforce fair sharing amongst the network hosts in the virtual circuit.
- A virtual circuit can ensure that a limited number of hosts or connections get preferential treatment.
A virtual circuit can partition the circuit by filtering the traffic by time of day, by VLAN range, by subnets or hosts, by particular application or application group, by traffic direction, and by capping the number of active connections or capping the number of active hosts within the virtual circuit. Any combination of these filters can be applied. For example, you can create a virtual circuit such that a particular branch (or subnet) is allowed a certain set of policies for inbound traffic (as direction) during off work hours (using a schedule).
A virtual circuit specifies its desired bandwidth either as kbps or as a percentage of it's parent circuit. When the sum of the desired bandwidths for all the virtual circuits within a circuit exceeds the circuit's bandwidth, the circuit is oversubscribed. Each virtual circuit specifies how it would like to deal with oversubscription. That is, either let the system automatically share the bandwidth amongst the virtual circuits, or specify a minimum bandwidth that is required.
Additionally, a virtual circuit can enable fair sharing amongst hosts in the virtual circuit. When fair sharing is enabled, the virtual circuit is called a dynamic virtual circuit and a further level of traffic shaping is introduced. Traffic is first shaped at the host level, then at the policy level. The bandwidth allocated will be the minimum of the two levels.
A virtual circuit can provide preferential treatment to a limited number of active hosts or to a limited number of active connections.

|
Note
When configuring a dynamic virtual circuit, the system will not allow the per host bandwidth to be less than 10 kbps, in which case the number of allowed hosts is calculated to be the virtual circuit bandwidth/10 kbps. Any hosts beyond the limit are then evaluated against later virtual circuits in the policy tree.
There is a system limit of 32,500 hosts that can fall into each dynamic virtual circuit. This may occur if the virtual circuit has more than 300 Mbps of bandwidth. When this limit is exceeded, hosts fall into the next applicable virtual circuit.
|

|
Best Practice:
It is a best practice to create an overflow virtual circuit immediately after a virtual circuit with a connection limit or a host limit, to capture the connections or hosts that were excluded.
|
Network objects are typically used when virtual circuits are created for specific branch office locations, or other subsets of the network, or user groups. Each branch office location or user group would be represented by a static network object or a dynamic network object (such as an Active Directory group). A default network object, private net, exists which defines all non-routable subnets. This can be used to create a virtual circuit for all WAN data.
The direction is used to ensure that the virtual circuit only captures traffic in a certain direction. This is useful for asymmetric circuits, as these generally require that at least two virtual circuits are defined - one for the inbound bandwidth and one for the outbound bandwidth.
Virtual circuits are part of the policy tree. To learn how circuits, virtual circuits, and policies work together, see Policy Tree.
 Where do I find this functionality?
Where do I find this functionality?
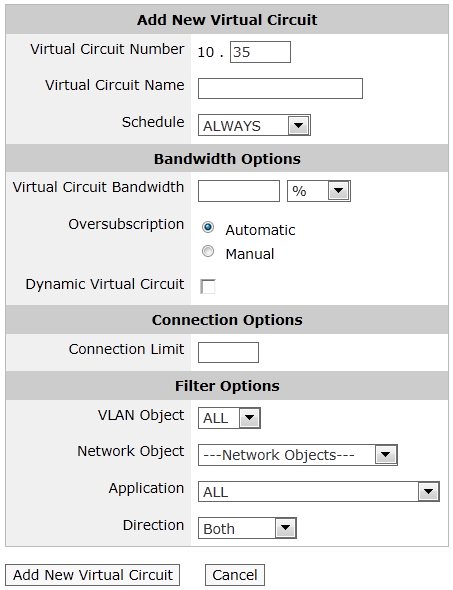
Go to Configuration > Traffic Policies > Optimizer > Optimizer, then click the Create New Virtual Circuit... link at the bottom of each circuit or edit an existing virtual circuit.
 To create a virtual circuit
To create a virtual circuit
- In the Virtual Circuit Number field, type the order of the virtual circuit in the policy tree.
- Enter a name for the virtual circuit.
- Optionally, specify a predefined Schedule, if you want this virtual circuit to be active for only a particular scheduled time period.
- Enter the desired Virtual Circuit Bandwidth as kbps or as a percentage of it's parent circuit.
 | Note The desired bandwidth for a single virtual circuit must not exceed it's parent circuit's bandwidth in either direction. |
|---|
-
Specify how to handle Oversubscription
- Automatic - The virtual circuits share bandwidth proportionally with other automatic virtual circuits after virtual circuits with manually set guaranteed bandwidth are accounted for.
- Manual - This virtual circuit is guaranteed a specified amount of bandwidth. The virtual circuits with manually set guaranteed bandwidth are allocated first; the remaining bandwidth is shared amongst the virtual circuits with automatically calculated guaranteed bandwidth.
 | Note The sum of all the manually set guaranteed bandwidths across the virtual circuits must not exceed the parent circuit’s bandwidth in each direction. If the sum of the manually set guaranteed bandwidths equals the parent circuits bandwidth, the virtual circuits with automatically determined guaranteed bandwidth will be guaranteed 0 bandwidth. |
|---|
- Optionally, check the Dynamic Virtual Circuit option, if you want to cap the number of active hosts in the virtual circuit or if you want to ensure fair sharing amongst the hosts. See the To enforce fair sharing among hosts or to cap the number of active hosts section below.
- Optionally, specify the Connection Limit, if you want to cap the number of active connections in the virtual circuit. Leave this field blank if you do not want to cap the number of connections.
 | Note Connections that arrive after the connection limit has been reached will be evaluated for inclusion in the following virtual circuits in the policy tree, potentially being caught in the catch-all virtual circuit. |
|---|
- Optionally, specify a VLAN Object to filter which traffic falls into the virtual circuit.
- Optionally, specify a Network Object to filter which subnet, hosts, users, or user groups falls into the virtual circuit.
- Optionally, specify an Application to filter which application or application group falls into the virtual circuit.
- Specify the Direction of traffic to capture in the virtual circuit.
The direction options are: Both directions, Inbound, and Outbound.
 | Note The direction is relative to the LAN. Consider an example where a network object and a direction is specified: |
|---|
'Internal' or 'External' network objects | Both | Only inbound and outbound traffic to and from the subnets defined by the network object. |
'Internal' network object | Inbound | Only inbound traffic to the subnets defined as 'internal' by the network object. |
| 'External' network object | Inbound | Only inbound traffic to the LAN from the subnets defined as 'external' by the network object. |
'Internal' network object | Outbound | Only outbound traffic from the subnets defined as 'internal' by the Network Object. |
| 'External' network object | Outbound | Only outbound traffic from the LAN to the subnets defined as 'external' by the Network Object. |
- Optionally, check the Dynamic Virtual Circuit option, if you want to enforce fair sharing. See 'To enforce fair sharing amongst hosts' below.
- Click Add New Circuit to add this virtual circuit to the policy tree.
- In the policy tree, change the ranking order of the virtual circuit, if necessary, to ensure the virtual circuit is in the proper order relative to the other virtual circuits in the circuit.
 Examples of handling virtual circuit oversubscription
Examples of handling virtual circuit oversubscription
Virtual circuits are oversubscribed when the sum of the virtual circuit bandwidths exceeds the parent circuit's bandwidth. For example:
Circuit Bandwidth = 3Mbps
- Virtual Circuit Bandwidth A = 2Mbps
- Virtual Circuit Bandwidth B = 1Mbps
- Virtual Circuit Bandwidth C = 1Mbps
This means, the sum of the three virtual circuits is 4Mpbs, but the circuit bandwidth is only 3Mbps.
|
VC A: automatic
VC B: automatic
VC C: automatic
|
Each VC gets:
desired bandwith / sum of VC bandwith * circuit bandwidth
- VC A = 2/4 * 3 = 1.5 Mbps
- VC B = 1/4 * 3 = 0.75 Mbps
- VC C = 1/4 * 3 = 0.75 Mbps
|
|
VC A: manual = 2 Mbps
VC B: manual = 0.5 Mbps
VC C: manual = 0.5 Mbps
|
Each virtual circuit with manually set oversubscription bandwidth will get their guaranteed amount
- VC A = 2 Mbps
- VC B = 0.5 Mbps
- VC C = 0.5 Mbps
|
|
VC A: automatic
VC B: automatic
VC C: manual = 0.75 Mbps
|
Each virtual circuit with manually set oversubscription bandwidth will get their guaranteed amount. Virtual circuits with automatic oversubscription calculations will share the remaining bandwidth as:
virtual circuit's desired bandwidth / total remaining bandwidth * (circuit's bandwidth - sum of manually specified oversubscription bandwidths)
- VC C = 0.75 Mbps
- VC A = 2/3 * (3 - 0.75) = 1.5 Mbps
- VC C = 1/3 * (3 - 0.75) = 0.75 Mbps
|
 To provide preferential treatment to a certain number of connections
To provide preferential treatment to a certain number of connections
On the Add New Virtual Circuit form:
- Specify the Connection Limit, if you want to cap the number of active connections in the virtual circuit. Leave this field blank if you do not want to cap the number of connections.

|
Note
Once a virtual circuit connection limit has been reached, it will no longer match any incoming traffic. Therefore, connections that arrive later will be evaluated against the remaining virtual circuits in the circuit. Once some of the active connections in the virtual circuit terminate, the virtual circuit will be used to match new traffic again.
|

|
Best Practice:
It is a best practice to create a virtual circuit immediately after a virtual circuit with a connection limit, to capture the connections that were excluded.
|
 To configure a dynamic virtual circuit (DVC)
To configure a dynamic virtual circuit (DVC)
Dynamic virtual circuits can be configured for fair sharing amongst the hosts or dynamic virtual circuits can be configured to limit the number of hosts so that those hosts get preferential treatment.
For fair sharing, you must specify how you would like the virtual circuit's bandwidth to be shared amongst the hosts. You can fix the per host bandwidth and have the system calculate the number of allowed hosts. Note that if there are less than the allowed hosts, each active host can burst to gain more bandwidth (if you have configured the virtual circuit to allow bursting). Or you can fix the number of hosts and have the system calculate the amount of bandwidth allowed per host. You can specify to automatically calculate the per host bandwidth and the number of allowed hosts. The system will then divide the virtual circuit's bandwidth by the number of active hosts.
On the Add New Virtual Circuit form:
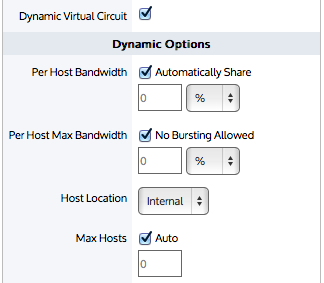
- Check the Dynamic Virtual Circuit checkbox.
-
Set the guaranteed Per Host Bandwidth that each host will receive.
- Automatically Share - The virtual circuit's guaranteed bandwidth is divided by the number of active hosts.
- Manually set bandwidth - Specify the guaranteed bandwidth amount that will be available to each host, if required. Specified as kb per second or as a percentage of the virtual circuit's guaranteed bandwidth.
-
Set the Per Host Maximum Bandwidth that each host is allowed.
- If No Bursting Allowed is selected, each host gets only the bandwidth that they have been guaranteed (above).
- Manually set bandwidth - Specify the maximum bandwidth amount that will be available to each host, if excess bandwidth is available.Specified as kb per second or as a percentage of the virtual circuit's available bandwidth.
-
Set the Location of the hosts to that will receive this fair sharing functionality.
Internal hosts are those that are on the LAN side of the appliance. External hosts are those that are on the WAN side of the appliance.
-
Set the maximum number of hosts that can be captured by this dynamic virtual circuit.

|
Note
When configuring a dynamic virtual circuit with the "automatically share” option enabled, the system divides the available bandwidth evenly among all of the hosts. The maximum number of hosts that can fit inside this type of DVC is the total bandwidth available divided by 10 kbps, with 10 kbps being the minimum allocated to each host. For example, if the available bandwidth was 100 kbps, the maximum number of hosts would be 10. Any surplus hosts are evaluated against later virtual circuits in the policy tree.
There is a system limit of 32,500 hosts that can fall into each dynamic virtual circuit. This may occur if the virtual circuit has more than 325 Mbps of bandwidth. When this limit is exceeded, hosts fall into the next applicable virtual circuit.
|
As examples, consider the following scenarios where the virtual circuit is defined to have 1024 kbps bandwidth in both directions and applies to a network object defining internal users and fair sharing is turned on.
|
Per Host Bandwidth: Auto
Per User Max Bandwidth: 100%
Host Location: Internal
Max Hosts: Auto
|
- If there is 1 internal host, it gets the full 1024kbps.
- If there are 2 hosts, they each get 512kbps and can burst up to the full 1024kbps (if the other user is not using their guaranteed 512kbps).
- If there are 10 hosts, they each get 102kbps and can burst up to the full 1024kbps, if available.
- If there are 102 hosts, they each get 10kbps and can burst up to 1024kbps, if available.
- If there are 103 hosts, the first 102 get 10kbps each. The 103rd host will not match this virtual circuit and will fall into the next applicable virtual circuit.
|
|
Per Host Bandwidth: 10%
Per User Max Bandwidth: No
Host Location: Internal
Max Hosts: Auto
|
- If there is 1 internal host, it gets 102kbps and cannot burst.
- If there are 10 hosts, they each get 102kbps and cannot burst.
- If there are 100 hosts, the first 10 hosts each get 102kbps and cannot burst. The remaining 90 hosts will not match this virtual circuit.
|
|
Per Host Bandwidth: 64kbps
Per User Max Bandwidth: 50%
Host Location: Internal
Max Hosts: 16
|
- If there is 1 internal host, it gets 64kbps and can burst up to 512kbps.
- If there are 16 hosts, they each get 64kbps and can burst up to 512kbps, if available.
- If there are 30 hosts, the first 16 hosts each get 64kbps and can burst up to 512kbps, if available. The remaining 14 hosts will not match this virtual circuit.
|
 Example to share the bandwidth equally amongst as many hosts as possible (using DVCs)
Example to share the bandwidth equally amongst as many hosts as possible (using DVCs)
- Check the Dynamic Virtual Circuit checkbox.
-
Set the DVC settings to:
- Per Host Bandwidth: Automatically Share
- Per User Max Bandwidth: 100%
- Max Hosts: Auto
This will ensure that the hosts will automatically share the bandwidth equally amongst the maximum number of hosts. If there are not many hosts, then those that are present are able to burst up to the maximum bandwidth.
For example: Consider a 50 Mbps virtual circuit bandwidth.
- If there is one host, it gets all 50 Mbps.
- If there are two hosts, they each get 25 Mbps.
- If there are 500 hosts, they each get 100 kbps.
- If there are 5000 hosts, they each get 10 kbps (which is the minimum that the DVC will allow)
- If there are more than 500 hosts, the additional hosts will not match this virtual circuit.
 Example to share the bandwidth equally amongst as many hosts as possible while ensuring a minimum bandwidth (using DVCs)
Example to share the bandwidth equally amongst as many hosts as possible while ensuring a minimum bandwidth (using DVCs)
- Check the Dynamic Virtual Circuit checkbox.
-
Set the DVC settings to:
- Per Host Bandwidth: The minimum bandwidth that you want the hosts to have
- Per User Max Bandwidth: 100%
- Max Hosts: Auto
This will ensure that the hosts will automatically share the bandwidth equally amongst the maximum number of hosts, where each host is guaranteed the specified minimum. If there are not many hosts, then those that are present are able to burst up to the maximum bandwidth.
For example: Consider a 50 Mbps virtual circuit bandwidth and 500 kbps minimum per host.
- If there is one host, it gets all 50 Mbps.
- If there are two hosts, they each get 25 Mbps.
- If there are 100 hosts, they each get 500 kbps. Note that 500 kbps x 100 hosts = 50 Mbps
- If there are more than 100 hosts, the additional hosts will not match this virtual circuit.
 Example to cap the bandwidth usage per host (using DVCs)
Example to cap the bandwidth usage per host (using DVCs)
- Check the Dynamic Virtual Circuit checkbox.
-
Set the DVC settings to:
- Per Host Bandwidth: Automatically Share
- Per User Max Bandwidth: No burst; set limit to your manual cap value
- Max Hosts: Auto
This will ensure that the hosts will automatically share the bandwidth equally amongst the maximum number of hosts, however no host will use more than the specified cap. If there are many hosts they will share the bandwidth equally, even if it means very little bandwidth per host.
For example: Consider a 50 Mbps virtual circuit bandwidth and a 1 Mbps cap per host.
- If there is one host, it gets 1 Mbps.
- If there are 50 hosts, they each get 1 Mbps.
- If there are 200 hosts, they each get 250 kbps.
- If there are 5000 hosts, they each get 10 kbps.
- If there are more than 5000 hosts, the additional hosts will not match this virtual circuit.
 Example to cap the bandwidth usage per host while ensuring a minimum bandwidth per host (using DVCs)
Example to cap the bandwidth usage per host while ensuring a minimum bandwidth per host (using DVCs)
- Check the Dynamic Virtual Circuit checkbox.
-
Set the DVC settings to:
- Per Host Bandwidth: The minimum bandwidth that you want the hosts to have
- Per User Max Bandwidth: No burst; set limit to your manual cap value
- Max Hosts: Auto
This will ensure that the hosts will automatically share the bandwidth equally amongst the maximum number of hosts, however no host will use more than the specified cap. If there are many hosts, each host will be provided a minimum bandwidth.
For example: Consider a 50 Mbps virtual circuit bandwidth and a 100 kbps guaranteed minimum bandwidth and a 5 Mbps cap.
- If there is one host, it gets 5 Mbps.
- If there are 10 hosts, they each get 5 Mbps.
- If there are 11-500 hosts, they each get 50 Mbps/number of hosts.
- If there are more than 500 hosts, the additional hosts will not match this virtual circuit.
 Example to limit the number of hosts sharing the bandwidth (using DVCs)
Example to limit the number of hosts sharing the bandwidth (using DVCs)
- Check the Dynamic Virtual Circuit checkbox.
-
Set the DVC settings to:
- Per Host Bandwidth: Automatically Share
- Per User Max Bandwidth: 100%
- Max Hosts: The maximum number of hosts that you want sharing the bandwidth
This will ensure that only your specified number of hosts will be managed by this virtual circuit. All the hosts in the virtual circuit will automatically share the bandwidth equally.
For example: Consider a 50 Mbps virtual circuit bandwidth and 100 hosts as a maximum.
- If there is one host, it gets all 50 Mbps,
- If there are ten hosts, they each get 5 Mbps.
- If there are 100 hosts, they each get 500 kbps.
- If there are more than 100 hosts, the additional hosts will not match this virtual circuit.
 Can I mistakenly prevent fully utilizing the bandwidth?
Can I mistakenly prevent fully utilizing the bandwidth?
If you set a bandwidth cap per host by setting the Per User Max Bandwidth and you set the maximum number of hosts, it is possible that you prevent access to excess bandwidth.
bandwidth-cap-per-host x number-of-hosts = allocated-bandwidth
If the allocated bandwidth is less than the virtual circuit bandwidth, then you are making some of the bandwidth inaccessible.
 Trouble-shooting virtual circuits
Trouble-shooting virtual circuits
If you are unsure whether traffic is being processed properly by the virtual circuit or the policies within your virtual circuit, it is best to use real time monitoring to determine if traffic is hitting your virtual circuit as you would expect.
- Go to the Monitor > Real Time > Conversations screen.
- Select Show Policies checkbox at the top of the screen to group the conversations by virtual circuit and policy.
- Look at the traffic falling under your virtual circuit to decide if the correct traffic is in there.
- If there is traffic that you were expecting that is not there, look in other virtual circuit groups to see where you expected traffic is.
- If your traffic is falling into the wrong virtual circuit, check the definition of the affected virtual circuits and ensure the most specific virtual circuit is higher in the policy tree.

