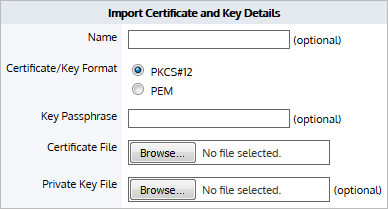
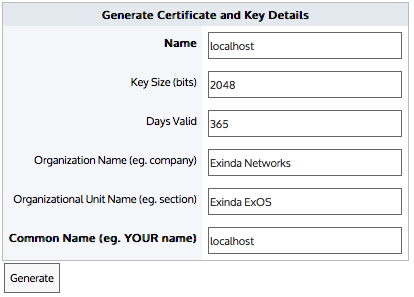
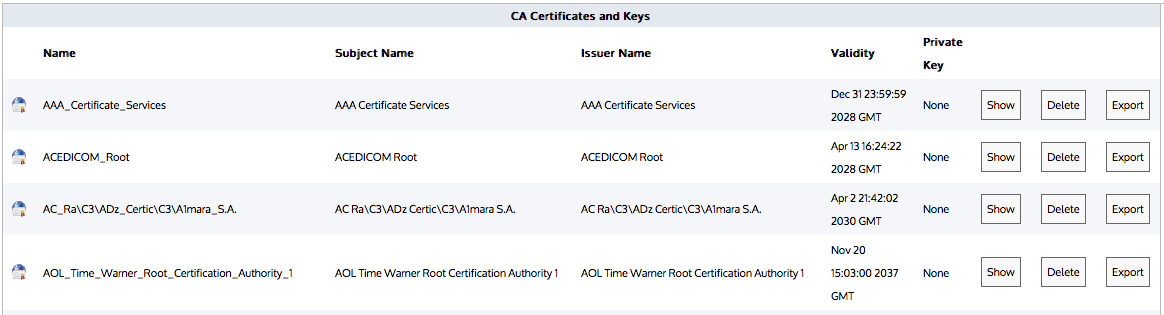
Note
Certificates and keys are stored securely on the Exinda appliance. It is not possible to export or view the private key once it has been imported. If you lose the configuration or need to migrate the configuration to another appliance, you must manually load the private key again.