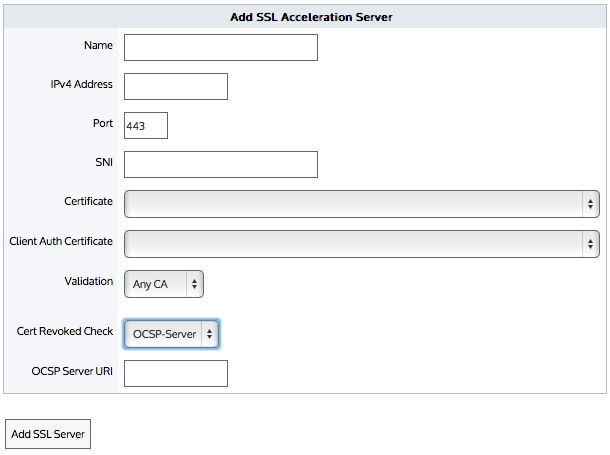
Note
If the revocation check cannot be done or the certificate has been revoked, then the SSL Acceleration Server is disabled. If the OCSP Responder is offline, the server is disabled. The appliance periodically tests the connection and re-enables the server when it is back up. If the OCSP response verification fails or if the certificate has been revoked, then the connection is reset and the server is disabled.