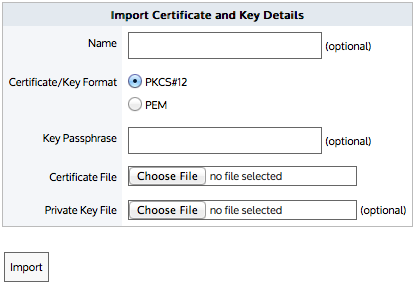
Use the following OpenSSL commands:
openssl genrsa -out myCompanyCA.key 2048
openssl req -x509 -new -key myCompanyCA.key -out myCompanyCA.cer -days 1000
-subj /CN="myCompany CA”
This will generate two files: a.key file and a .cer file that can be uploaded in the CA certificates UI.